By Rob Burkett, Principal, Banking & Credit Union Solutions and Greg Grinberg, Director of Technology
Salesforce Platform Encryption offers financial institutions the benefit of an additional level of security without the tradeoffs that come with standard encryption. In our previous post, How to Get the Most Out of Salesforce CRM Platform Standard Security Tools, we reviewed which out-of-the-box Salesforce security features are most beneficial to financial institutions and how to leverage them to their fullest potential.
To take your security measures further, Salesforce Shield provides a more robust suite of solutions. Shield includes three products: Platform Encryption, Event Monitoring, and Field Audit Trail. We’re going to focus on Shield Platform Encryption, which provides a higher-level encryption (256-bit instead of 128-bit) than the classic offering, along with more in-depth options that financial institutions may want to consider implementing.
Platform Encryption gives you increased control over:
- Fields: Encrypt more fields than with standard encryption (ex: most custom text, url, email, phone and date fields and some standard fields are available). Decrypt fields when needed.
- Files and attachments: Added capability to encrypt your documents.
- Platform functionality: Enjoy capabilities not included with standard encryption (ex: workflow rules, formula fields, additional SOQL query options, etc.)
- Security: Prevent attackers from accessing your data if SFDC’s tenant architecture is compromised, since you have your own tenant secret and can bring your own keys.
Shield can take your security tools to the next level, but it isn’t a silver bullet.
Platform Encryption DOES NOT:
- Prevent non-authorized users from accessing your Salesforce org
- Prevent authorized users from viewing specific data
- Prevent authorized users from exporting customer data
How Do I Start With Shield Platform Encryption?
Before you determine that Platform Encryption is needed, get Compliance & IT involved, establish threat models, and decide if standard Salesforce tools will satisfy your needs.
Include Compliance & IT In All Decisions
It is important to understand what you need from a compliance standpoint and balance that with the user’s experience, as we discussed in our 10 Keys to Digital Transformation: Governance. Encryption serves a purpose, but it comes with tradeoffs that can negatively impact system performance (i.e., reporting limitations, formula fields, criteria-based sharing rules, deduplication tools, etc.).
We frequently see Salesforce make it through a bank’s internal security review, the project starts, and oftentimes, compliance & IT aren’t involved until the end of the project. Delaying transparency with IT and compliance teams presents problems for the very people tasked with developing and maintaining an information security program, setting up controls, and performing regular audits.
Delayed project transparency also results in a mad rush toward the end of the project to re-review the security that’s put in place and evaluate the need for Salesforce Shield (specifically Platform Encryption) with the idea that more protection is always better — right?
Of course! However, just like other methods of increased security, there are trade-offs that should be measured against functionality gains. Shield is an additional cost in terms of real dollars and human resources. This adds another metric to your decision-making tree, especially if you are at the end of your project.
When a business ensures IT and compliance teams are part of the planning process, a project is smoother with less rework, better team alignment, and optimal outcomes. It eliminates the possibility of an adversarial relationship by ensuring everyone is working towards the same goal, striving towards the same finish line.
How that finish line is decided is another important part of the process.
Define the Finish Line With All Stakeholders
It’s important to work with compliance and executive management early on to set the ground rules and establish your success criteria for a completed project.
Implementations vary in length, but you can plan on the following:
- Compliance & IT deliverables
- Documented security program for Salesforce
- Documented threat models & controls
- Approval of security program timeline
- Final approval and go-forward plan
Threat Models help anticipate ways in which your data will be compromised and attempt to mitigate risk, making them a worthy addition to project completion criteria.
Some common examples of threat modeling are:
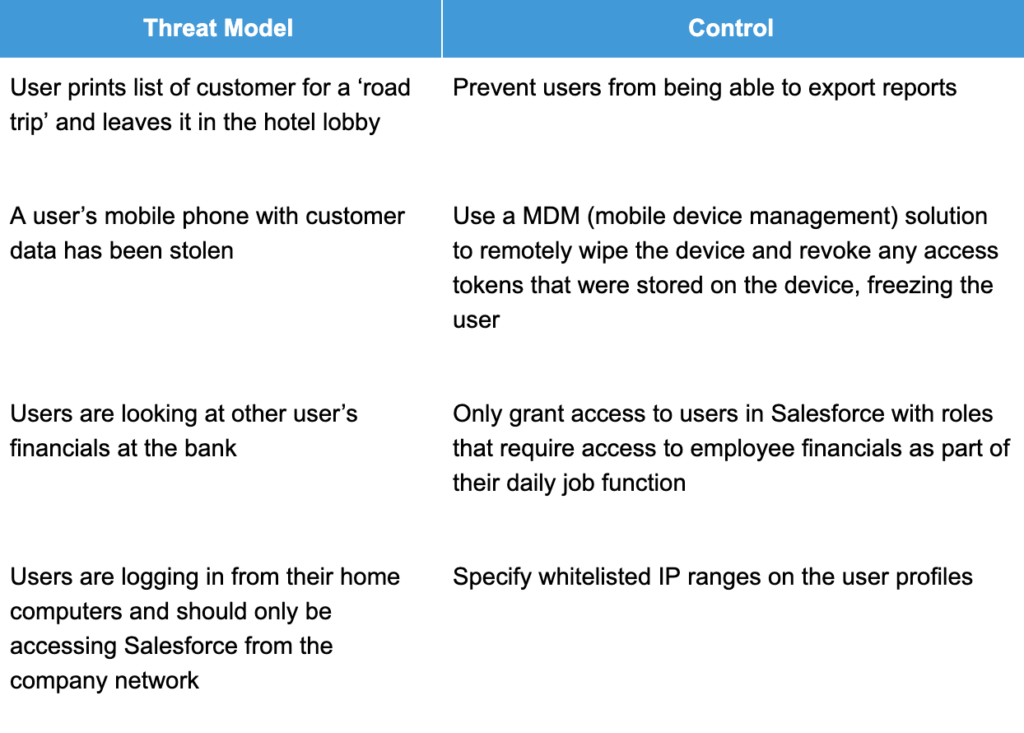
Shield encryption is an added level of security that can handle many of the common challenges not addressed by standard platform encryption. The common thread through each use case involves multiple teams, from IT and compliance to executive-level leaders, to ensure your business gets the most out of every security feature and leverages them to their full potential.
Still on the fence about choosing between the security features available through standard encryption or Shield encryption? Ready to hear more about how Shield can augment your existing Salesforce instance? Let’s chat.


