Reading Time: 6 minutes
When deciding what tools and processes to adopt for your digital transformation, you need to keep DevSecOps front of mind. If you evaluate the security risks in your existing or planned development and release process, you can make sure the right tools and processes are in place to mitigate these risks.
First, evaluate your process end to end. Different teams will identify different risks, and the likelihood or severity of those risks will also vary. But a typical development and release process will have vulnerabilities such as:
- Unauthorized metadata changes being made in production
- Bugs and errors being released to production
- Code failing silently in production due to breaking changes
- Sensitive data being deployed to testing environments during sandbox seeding
- Data getting lost or corrupted in production due to user error, malicious actions, or faulty integrations
- Sensitive records being exposed because permissions metadata gets corrupted
- Metadata being lost or corrupted due to a risky release
Next, consider what your process will look like as it evolves. Will new risks be introduced? Will the likelihood and severity of risk be increased? You need tools and processes that can scale with you to ensure continued and enhanced security and efficiency.
Having identified the risks, it’s easier to establish what security measures you need and what DevSecOps will look like for your team. In general, you need tools and processes for the following:
- Visibility: You need to see when anything is going wrong, so you can respond quickly but also so you can have confidence that things are secure the rest of the time.
- Mitigation: The severity of most risks can be reduced. Some risks can be eliminated altogether.
- Restoration: When a fault or incident occurs, you need tools and processes that help you recover quickly and reliably.
More specifically, here are seven key DevSecOps tools and processes that your team should consider.
1. Backup and restore
Backups are fundamental for security. But it’s not obvious to every business that they need to back up their Salesforce orgs. Gearset’s State of Salesforce DevOps 2022 report shows that 27% of teams don’t regularly back up their orgs, and 41% haven’t implemented a backup solution for Salesforce data.
Putting in place a tried and tested backup and restoration solution for both Salesforce data and metadata should be a top priority for any team thinking about DevSecOps. Some teams manually back up data for peace of mind, but would struggle to restore that data in the event of severe data loss because they don’t have backup metadata to restore the shape of the org first. Other teams have a mature DevOps process that effectively safeguards their metadata, but data backups are overlooked. Either way, these teams aren’t prepared for disaster recovery.
Backups work best when they’re woven into a broader DevSecOps process. The team responsible for managing releases should be able to back up production on demand before a risky release, without switching between tools. And when a team comes to restore lost data or corrupted metadata, using familiar deployment workflows to restore boosts confidence and accelerates time to recovery.
2. Monitoring and alerts
Monitoring tools give you full insight into the state of your org. Specifically, you need to keep track of the changes to data and metadata in production.
The ability to make declarative changes within Salesforce is one of its key strengths. But it’s also a potential weakness if people continue making changes directly in production when their team has put in place a proper release management process. Metadata monitoring allows you to identify any such changes in production, making sure that everything is accounted for in your audit trail — even changes made outside the usual process. Problematic changes can be identified and removed, while hotfixes can be deployed back and synced with other environments, such as your Git repository if you’re using version control.
Keeping an eye on the data in your org poses a different problem. Data changes all the time, so it’s no good trying to keep track of every record that’s added, changed, or deleted. But it is important to know when something unusual has happened, such as hundreds of contacts being deleted suddenly. A configurable system such as the smart alerts tool in Gearset’s backup solution lets you specify what levels of data churn might indicate a security incident for your business.
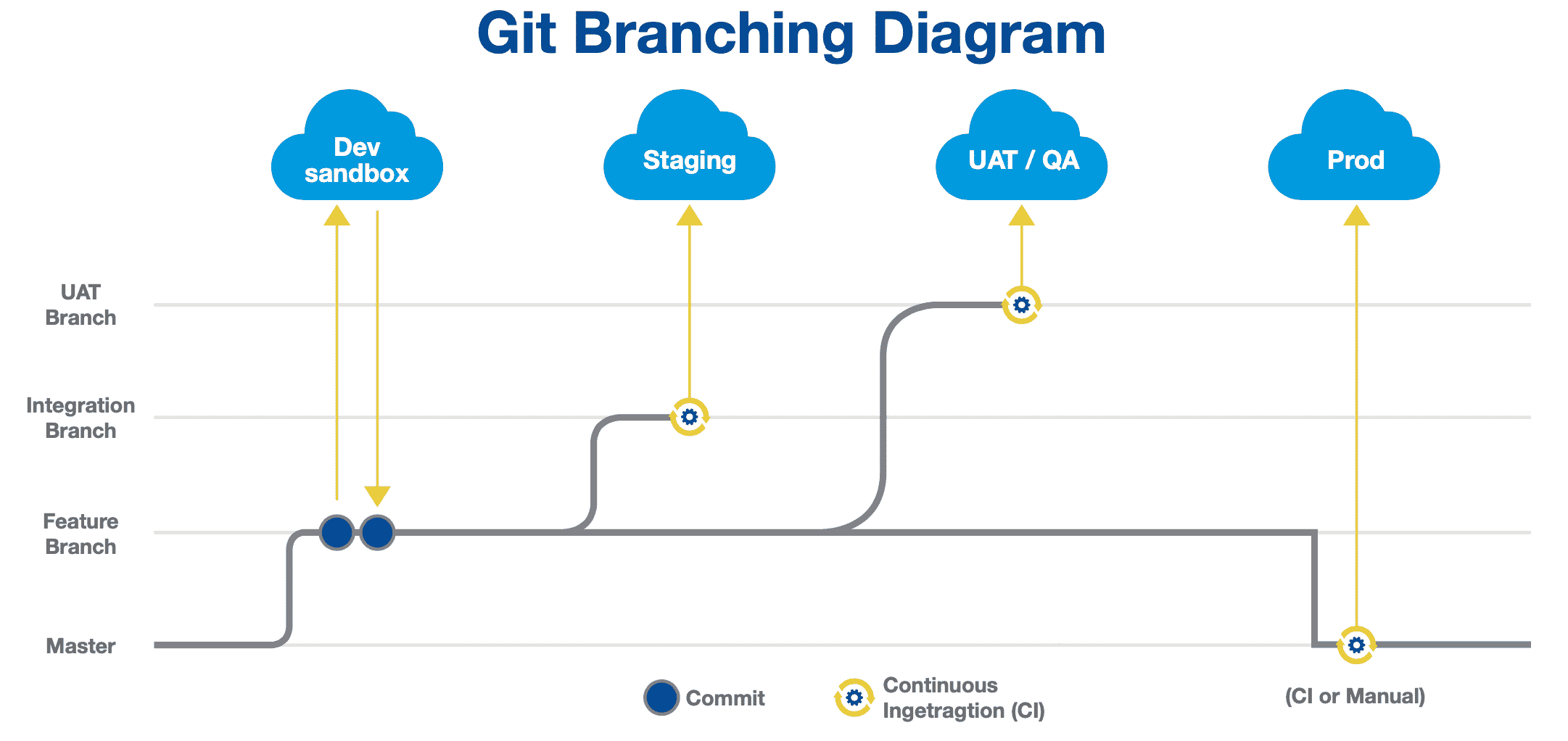
3. Version control
Version control is fundamental to DevOps, and also brings significant security benefits. Git enables teams to collaborate effectively and enforces workflows that make the release process more robust. Instead of production being the single source of truth for your team, and so a single point of failure, the metadata in production is backed by a new source of truth: the main branch. The metadata in main should always be deployable so that your team can release the latest version of your metadata on demand.
A source-driven workflow should involve teammates reviewing each other’s pull requests to merge new work into the main branch. This improves the quality of work and builds a culture of collaboration, helping teams to catch bugs and errors long before they’re released to production. Git also automatically generates an audit trail of all pull requests and commits, which makes it easier to debug releases. Teams can see who made what change when and why. And, when the need arises, Git supports reverting merges and rollbacks to earlier states.
4. CI/CD
Once teams have adopted version control successfully and built a release pipeline around their chosen Git branching strategy, they’re ready to begin automating parts of that pipeline. The aim is to automate repeatable steps for promoting work along the pipeline: the continuous integration (CI) of each developer’s work into one environment and the continuous deployment (CD) of all this work to environments such as QA or UAT (user acceptance testing).
Automation encourages short iterative processes and is therefore an essential part of DevSecOps, which is all about working in an agile way to accelerate your release cadence. Smaller, more frequent releases don’t just get value into end users’ hands sooner and shorten feedback loops. They also make it easier to recover from any issues because it’s easier to debug a small release — there’s less code and configuration to look at!
A lightning-fast release process also means teams can respond quickly when a bug is identified. Often the response will be to roll forward, getting the fix out in the next release and making that release as soon as possible. If that’s not possible, teams need to roll back the release that broke things — something that’s more straightforward with smaller releases.
5. Test automation
The purpose of testing is, of course, to improve work and reduce the likelihood that anything substandard or even dangerous is released. Folding test automation into your DevSecOps process usually means having tests run at several stages of the release cycle, which dramatically improves security.
Unit testing makes sure your Apex classes execute as intended. Testing code before it’s released obviously reduces the risk that faulty changes make it as far as production. But it’s equally as important that you continue testing the code already in production. If code begins to fail silently, you’ll only notice once it begins to cause damage. Automated unit testing of all the Apex in your org allows you to monitor these tests and rectify code after a breaking change. It also tracks your code coverage, so you never fall below the 75% threshold at which Salesforce will no longer allow you to deploy. Remember, it’s a key principle of DevSecOps that you should be able to release on demand.
Static code analysis, another form of testing that can be automated, improves code quality. It doesn’t execute your Apex classes to observe the output, but searches your code for anything that your team has agreed to avoid. Rulesets for code quality include rules ensuring the security of code. For instance, PMD includes a rule that checks redirects in an Apex class are not made to user-controlled locations, preventing attackers from redirecting users to phishing sites.
6. Data masking
In addition to their automated tests, most teams manually test that their changes behave as intended by deploying them to a QA, UAT, or Staging environment and verifying their behavior. Usually this environment is a full or partial sandbox — a replica of Production in terms of metadata and perhaps also data. Data is vital for the most robust testing. The quirks found in real-life datasets provide the edge cases that might cause a new feature to fail, and this is why teams often want production data in their testing environment.
The security implications of this are clear: copying sensitive data, perhaps including personally identifiable information, to another org doubles the risk of unauthorized exposure. Data masking solves this dilemma by allowing you to obscure the production data you deploy to testing environments, so you can carry out robust testing procedures without compromising on security or breaching compliance requirements.
7. Everything depends on deployment success
For Salesforce, specifically, none of the above can be achieved until deployments are running quickly and reliably. Successful deployments are the foundation on which DevSecOps stands. Since the platform-native tooling for deployments has a success rate of approximately 50% and can take teams upwards of 10 hours for each deployment, teams practicing DevSecOps must use other deployment tools.
Solving the problem of slow and error-prone deployments unlocks the door to DevSecOps, and third-party solutions such as Gearset are being used by thousands of teams to build modern workflows that incorporate version control, automated testing, CI/CD, and more.
Secure your org with DevSecOps
At Silverline, we look at ourselves as facilitators to bring business and security stakeholders together to negotiate the benefits of features vs. security, and future-proofing development and costs. We provide a point of view on Salesforce security best practices, and our audits and workshops help educate our clients across all their various roles. Learn more about how we can help your organization.